inspiration from (http://www.infosightinc.com/IT-Security/data_loss_prevention.php)
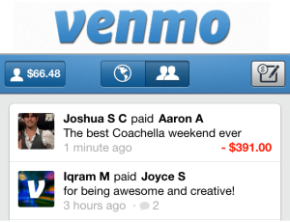
Overall the applications did secure the users PII, but there was some data leakage that gave me information about the user and their transaction history. However, it’s important to note that user’s financial information and personal identifiable information is secure when using the applications.
How do I know?
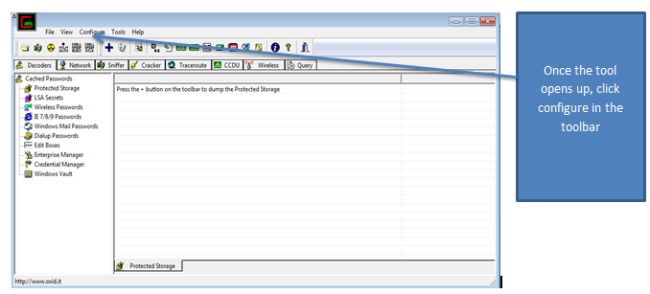
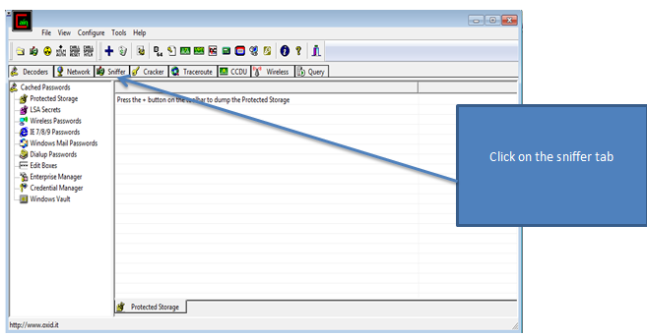
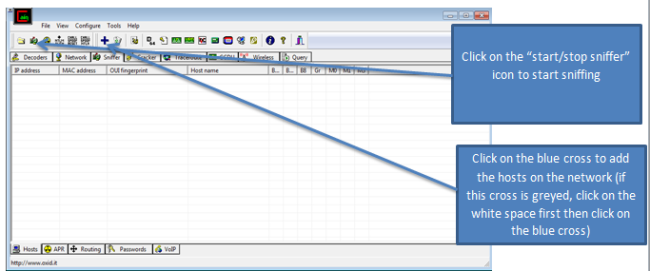
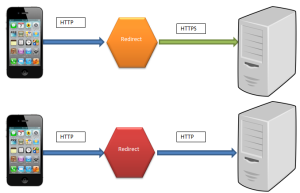
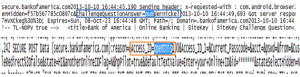
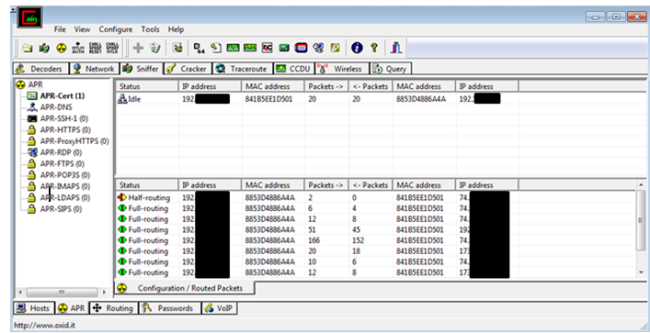
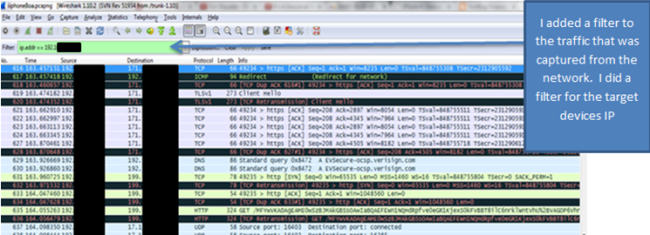
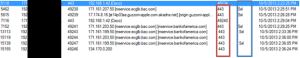
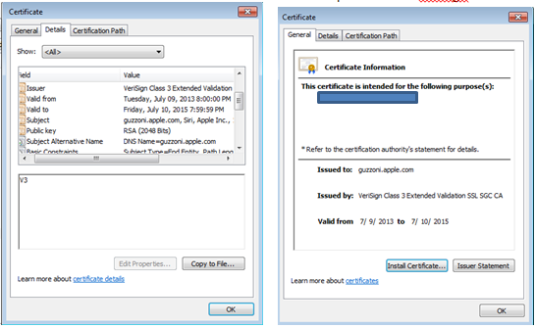
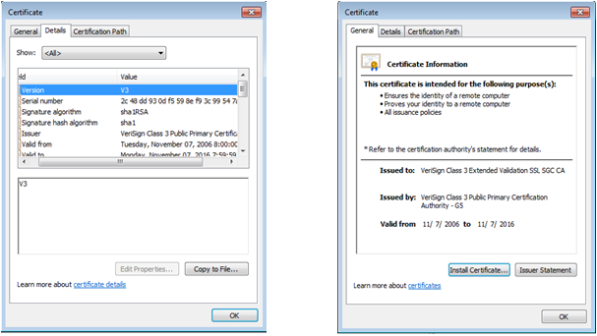
Well, by monitoring the data sent over the network using an Arp spoof attack. I wasn’t able to see financial information sent that has been over the network. By using WireShark to capture the packets sent over the network, I was only able to confirm that the applications are using port 443 to send data over the network. I was also able to confirm that apps are using certifications like VeriSign to ensure authorization when the users logs into the application. Using Paraben’s Device seizure to view the data stored on the devices, I was able to see that data stored didn’t contain any financial information or Personal Identifiable information (PII). However, depending upon the application, data that contained user information, card description, and transaction information was stored on the device. Some information was encrypted and some information was stored in plaintext.



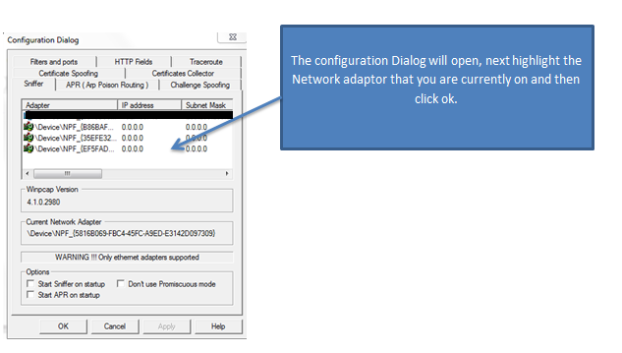
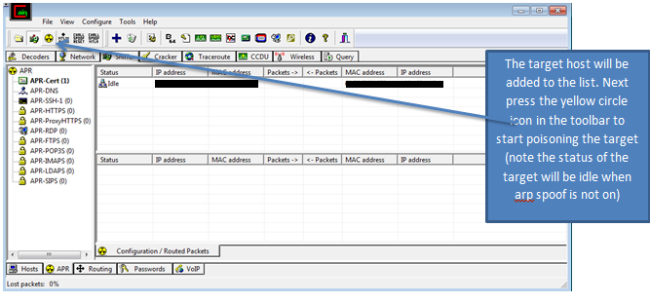
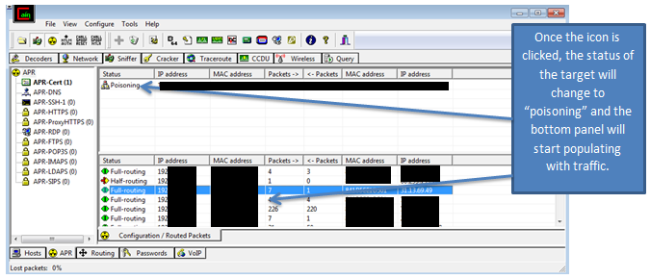



 (
(